June 20, 2025
Invisible Intelligence

How Augment 1x Remains Undetectable in Interviews, Exams, and Screen-Shares
Posted by Amanda
6 minutes read
Invisible by Design
Imagine joining a coding interview on HackerRank, sharing your desktop through Zoom, all while LockDown Browser periodically scans your windows. In the background, Augment 1x quietly captures GPU frames, interprets your IDE context, and softly delivers algorithm suggestions through your earbuds—no extra windows, cursor glitches, or suspicious CPU spikes. Zoom and other tools only share what you intend, as Augment 1x operates from a secure overlay, hidden even from desktop recording tools.
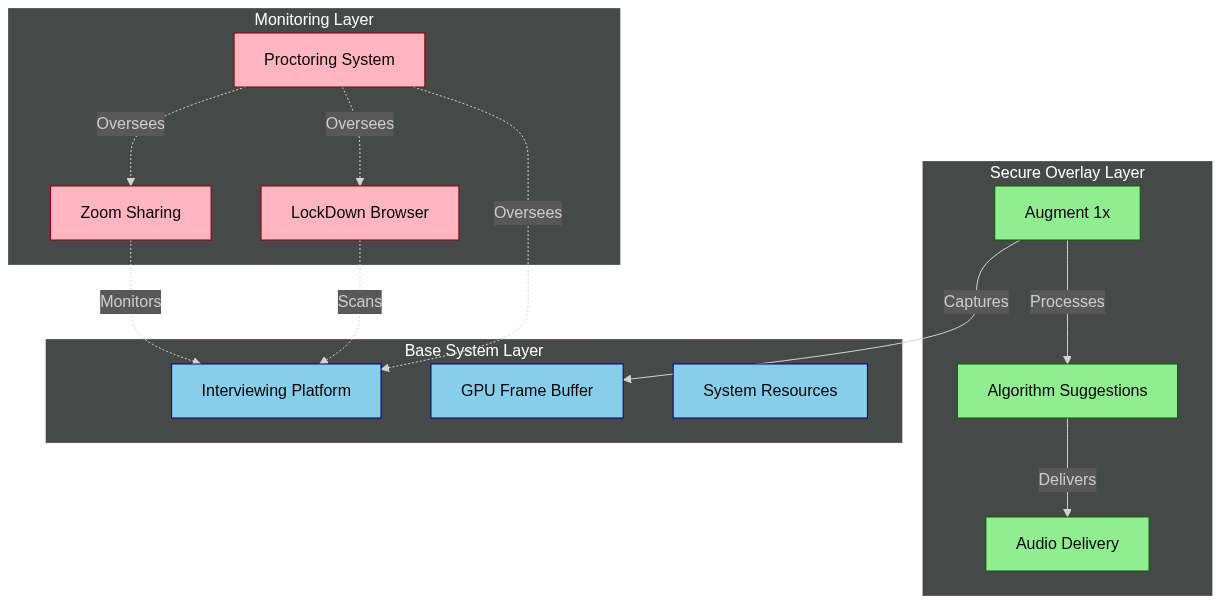
Why Detection Tools Fail to Spot Augment 1x
Modern monitoring tools rely on defined browser and desktop security boundaries. Augment 1x exploits no loopholes but carefully inhabits legitimate blind spots these tools inherently leave open. Browser Limitations
- Websites can detect when you switch tabs, paste content, or access your webcam if permitted.
- Websites cannot inspect running applications, access other windows' content, or monitor GPU frames.
Desktop Monitoring Constraints
- Tools like Honorlock or LockDown Browser add extra scrutiny but still respect OS restrictions, typically running without administrative privileges.
- They can identify open windows, capture screens, and monitor basic CPU usage.
- They cannot, without intrusive drivers, capture hidden overlays, protected GPU buffers, or discreet global hotkeys. Augment 1x precisely leverages these legitimate operational gaps, ensuring its assistance remains undetectable.
Engineering for Complete Stealth
Augment 1x's invisibility strategy is multi-layered:
- Window Enumeration: Uses hidden, tool-style overlays (WS_EX_TOOLWINDOW).
- Screen Capture Resistance: Renders visuals in secure DirectComposition surfaces exempt from mirror outputs.
- Process Integrity: Mimics benign system utilities without DLL injections or suspicious handles.
- Performance Masking: Maintains low resource usage with dynamic throttling, keeping activity within normal fluctuations.
- Discreet Inputs: Registers global hotkeys without focus shifts or detectable events. The result: complete invisibility during high-stakes tasks, whether screen-sharing, live coding, or exam proctoring.
Instantaneous Support, Zero Suspicion
Every millisecond counts. Augment 1x's entire pipeline—capture, encode, fuse, act—completes in under 40 milliseconds, ensuring immediate, undetectable assistance indistinguishable from ordinary computer activity.
| Stage | Time (ms) |
|---|---|
| Capture | ≤ 5 |
| Encode | ≤ 15 |
| Fusion | ≤ 10 |
| Action | ≤ 10 |
The Bottom Line
Augment 1x stays off-radar because it intelligently exploits intentional blind spots in browser and desktop monitoring frameworks. Without compromising your computer's security or needing suspicious workarounds, Augment 1x remains completely invisible—even during intense scrutiny like live screen-sharing or rigorous exams. Next: "Adaptive Prompt Crafting at 30 FPS" – How Augment 1x anticipates your questions before you ask.